While some articles about the 28c3 talk were quite acruate and neutral, others were a little more sensionalists and probably generalised the topic a little too quickly.
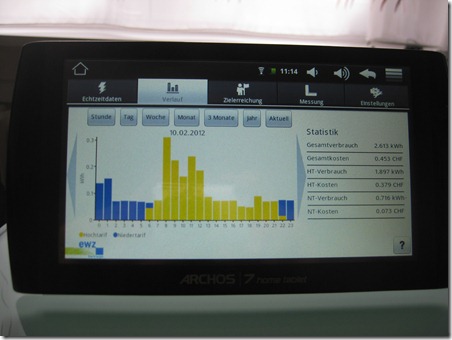
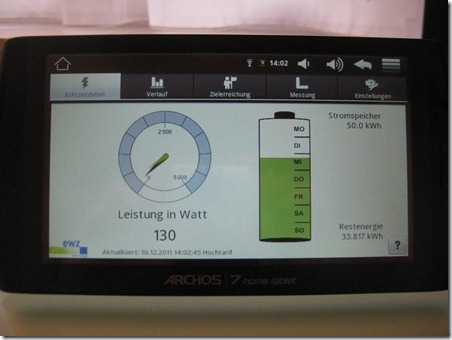
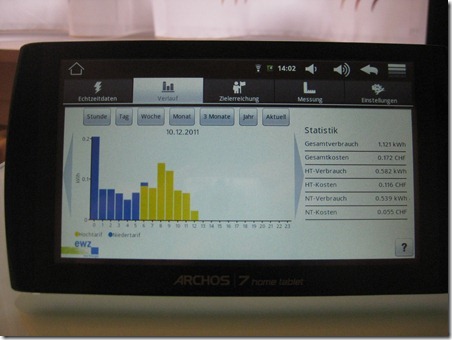
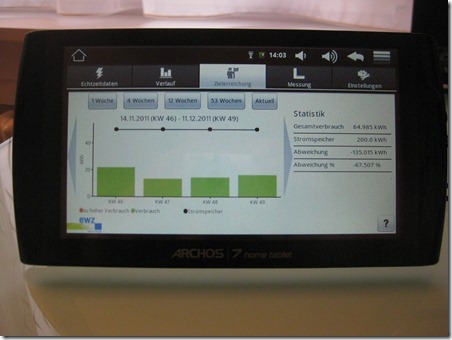
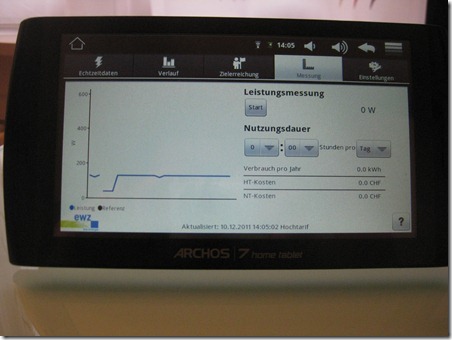
As a happy owner of such a smart meter in the context of a study, I wanted to have a closer look at the security of my installation. As mentioned in the previously linked article, there is as far as I’m aware no direct data connection back to the EWZ on the occasion of this study. Data is kept for a few weeks on the smart meter and retrieved by the Android tablet and stored on this device. This is also the reason why I must start the Android tablet at least every couple of weeks, ensuring that no data gets lost.
So no Internet connection in our EWZ study – and therefore a lot less potential problems ![]() . Let’s have a look how the data transfer between the smart meter and the tablet is done.
. Let’s have a look how the data transfer between the smart meter and the tablet is done.
The first communication between the smart meter and the flat is done using a Devolo device over the electric wiring. I’m not aware of any special security problem for this technology, so let’s assume for now we’re safe there.
Once in the flat, the information transits via a second Devolo device which sends the feed to the Android tablet over WiFi. A closer look about the used settings (on Windows, run netsh wlan show all in a console) shows that they are pretty safe as WPA2 is in use:
SSID [XX] : ewz[SOME_NUMBERS]
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : [BSS_MAC_ADDRESS]
Signal : 99%
Radio type : 802.11n
Channel : 2
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
But is there even a way to snoop some of the traffic and get a better understanding of this solution? Having your neighbour cracking the WPA2 password of the Devolo is possible, but I tend to disconnect it once I’m done with the tablet anyway – another layer of security to bypass for an attacker wanting to “hack” my smart meter.
The key – as a local curious person – to gain access to the network traffic is to exploit one of the three ethernet connectors of the Devolo device which also serves as WiFi Access Point. The network traffic shown below is therefore only accessible to local attackers which either have access to the AP, the smart meter or maybe via the electrical wire.
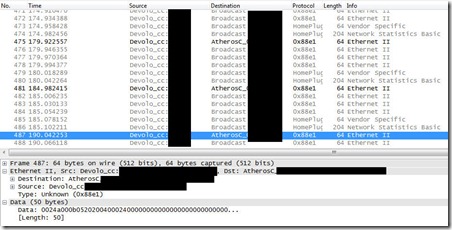
In a standard usage, we see a broadcast on a low network level of 50 bytes of data every 2 seconds. This matches exactly the immediate consumption update the tablet gets:
The data field therefore certainly contains the measurement, which is readable by anyone which can see the broadcast. But as said before, this is limited to local attackers (unless flaws exist in the Devolo devices which I don’t know about).
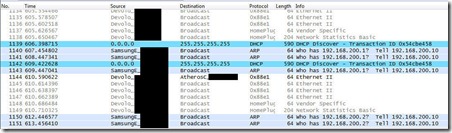
When shuting down the tablet and restarting it, we get a more interesting capture were we have what seems to be a fixed IP address 192.168.200.10 looking for 192.168.200.1.
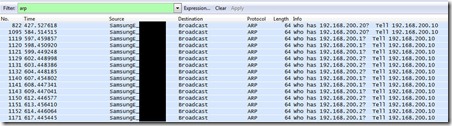
Filtering all the captured traffic for only ARP requests show that the Android device tries to successively find:
A ping confirms that addresses 192.168.200.10 & 192.168.200.20 are valid IP addresses in this configuration, but that 192.168.200.20 seems either way slower or further away than 192.168.200.10:
C:\>ping 192.168.200.10
Pinging 192.168.200.10 with 32 bytes of data:
Reply from 192.168.200.10: bytes=32 time=4ms TTL=64
Reply from 192.168.200.10: bytes=32 time=1ms TTL=64
Reply from 192.168.200.10: bytes=32 time=1ms TTL=64
Reply from 192.168.200.10: bytes=32 time=1ms TTL=64
Ping statistics for 192.168.200.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 4ms, Average = 1ms
C:\>ping 192.168.200.20
Pinging 192.168.200.20 with 32 bytes of data:
Reply from 192.168.200.20: bytes=32 time=17ms TTL=255
Reply from 192.168.200.20: bytes=32 time=11ms TTL=255
Reply from 192.168.200.20: bytes=32 time=7ms TTL=255
Reply from 192.168.200.20: bytes=32 time=7ms TTL=255
Ping statistics for 192.168.200.20:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 7ms, Maximum = 17ms, Average = 10ms
The suspicion that 192.168.200.20 is the Smart Meter itself turns into a final confirmation by an nmap scan of the network, where aside the scanning machine only two other hosts answer:
C:\>nmap 192.168.200.10/24 -p80 Starting Nmap 5.50 ( http://nmap.org ) at 2012-02-13 16:34 W. Europe Standard Time Stats: 0:00:35 elapsed; 64 hosts completed (2 up), 66 undergoing Host Discovery Parallel DNS resolution of 1 host. Timing: About 0.00% done Nmap scan report for 192.168.200.10 Host is up (0.00s latency). PORT STATE SERVICE 80/tcp filtered http MAC Address: 00:02:XX:XX:XX:XX (Samsung Electro-Mechanics Co.) Nmap scan report for 192.168.200.20 Host is up (0.00s latency). PORT STATE SERVICE 80/tcp filtered http MAC Address: 00:0F:XX:XX:XX:X (Landis+Gyr)
Based on these observations, we can see that the whole EWZ Smart Meter setup is way more secure than the example given during the 28c3 talk. There are still possibilities to “hack around”, such as looking at the behaviour of the tablet if IP 192.168.200.1 or 192.168.200.2 start to answer (e.g. are they used as gateways or configuration servers?) but this would void the written agreement with the power company about not interfering with the measurement devices.
Read all the articles about the EWZ Smart Meter using the tag SmartMeter